Microsoft Security Threat Intelligence has been tracking multiple ransomware campaigns by a group known as DEV-0270 who also goes by the alias Nemesis Kitten.
Who is DEV-0270?
DEV-0270, a sub-group of the Iranian threat actor known as PHOSPHORUS, are known for leveraging newly disclosed vulnerabilities against their targets. If successful, the group contacts the victim within a couple days of the ransom note and demands $8000 for the decryption keys. Microsoft noted: “In one attack, a victim organization refused to pay the ransom, so the actor opted to post the stolen data from the organization for sale packaged in an SQL database dump.”
How do they operate?
DEV-0270 is opportunistic and scans the internet for vulnerable servers. In several instances, known vulnerabilities in Exchange were exploited, ProxyLogon being the most prevalent.
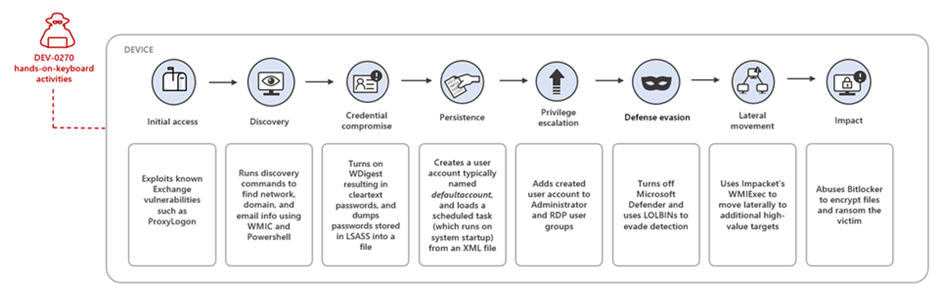
According to Microsoft, the typical attack chain is as follows:
- Initial Access: Exploits known Exchange vulnerabilities such as ProxyLogon
- Discovery: Runs discovery commands to find network, domain, and email info using WMIC and Powershell
- Credential compromise: Turns on WDigest resulting in cleartext passwords, and dumps passwords stored in LSASS into a file
- Persistence: Creates a user account typically named ‘defaultaccount’ and loads a scheduled task (which runs on system startup) from an XML file
- Privilege Escalation: Adds created user account to Administrator and RDP user groups
- Defensive Evasion: Turns off Microsoft Defender and uses LOLBINs to evade detection
- Lateral Movement: Uses Impacket’s WMIExec to move laterally to additional high-value targets
- Impact: Abuses Bitlocker to encrypt files and ransom the victim
Recommended Mitigation
Techniques used to target Microsoft Exchange Servers may be mitigated by:
Apply the corresponding security updates for Exchange Server, including applicable fixes for CVE-2021-26855, CVE-2021-26858, CVE-2021-26857 and CVE-2021-27065.
The same recommendation applies to unpatched internal Exchange Servers.
- Use Microsoft Defender Firewall
- Enforce strong local administrator passwords. Use tools like LAPS
- Ensure that Microsoft Defender Antivirus is up to date and that real-time behavior monitoring is enabled
- Keep backups so you can recover data affected by destructive attacks
Read more: Microsoft Exchange Server Security: The 10 Best Ways to Secure Your Server
Reach out to Messageware to Improve Microsoft Exchange Server Security
If you are not protecting all the protocols used by your Exchange Server, you’re putting your company at a higher risk of a data breach.
Security incidents happen frequently. They cause disruption, loss of data and place your company’s reputation at risk.
Have you heard about Messageware’s EPG that offers advanced Exchange Server security to protect organizations from a variety of logon and password attacks, as well as extensive real-time reporting and alerts of suspicious logon activity? Click here to learn more.
