Microsoft’s 365 Defender Research Team recently investigated an attack in which malicious OAuth applications were deployed on compromised cloud tenants.
Initial Access
The attacker first needed to compromise a cloud user’s account that had sufficient permissions in order to create a malicious OAuth application.
The threat actor did this by launching credential-stuffing attacks against high-risk accounts that didn’t have multi-factor authentication (MFA) enabled. They then leveraged the unsecured administrator accounts to gain initial access, said the research team.
Once the attacker had access to the cloud tenant, they created an OAuth application that added an inbound connector in the email server. The threat actor then used the malicious inbound connector to send spam emails that looked like they originated from the target’s domain. They sent the spam emails as part of a deceptive sweepstakes scheme meant to trick recipients into signing up for recurring paid subscriptions.
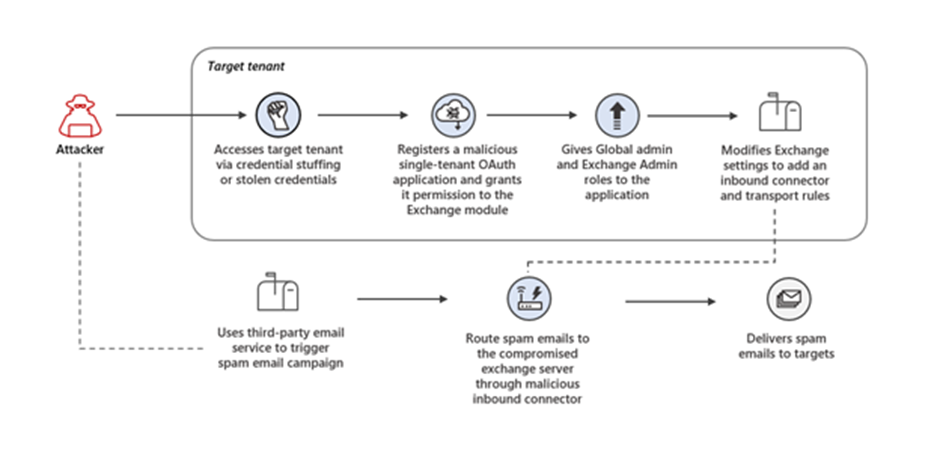
Based on the high success rate of authentication attempts, it is likely the attacker used a dump of compromised credentials. The 365 Defender Research Team’s investigation revealed that 86% of the compromised tenants had at least one admin with a real-time high-risk score. It is also important to note that all the compromised administrators had multi-factor authentication turned off, which could have stopped the attack.
In the past few years, Microsoft has observed an escalation in threat actors, including nation-state actors, using OAuth applications for malicious purposes.
Reach out to Messageware to improve Microsoft Exchange Server Security
If you are not protecting all the protocols used by your Exchange Server, you’re putting your company at a higher risk of a data breach.
Security incidents happen frequently. They cause disruption, loss of data and potentially risk the reputation of your company. However, if you implement these steps, you’re doing more than most other companies.
Have you heard about Messageware’s EPG that offers advanced Exchange Server security to protect organizations from a variety of logon and password attacks, as well as extensive real-time reporting and alerts of suspicious logon activity? Click here to learn more.
