In this article, we’ll answer frequently asked questions about how to manage your Active Directory Lockout policy. There is no one-size-fits-all approach to customizing these settings as organizations have different risk levels. For helpful information about what causes frequent Active Directory account lockouts, check out our blog “6 Common Causes of Active Directory Account Lockouts and How to Fix Them.”
Table of Contents:
How to view policy using Server Manager
How to view policy using Command Line or Powershell
How to view policy using Windows Search
What do Active Directory Settings Mean
How to check if an Active Directory account is locked using Event Viewer
How to check if an Active Directory account is locked using PowerShell
How to Change the Number of Tries Before Active Directory Lockout
How to Set Account Lockout Duration
Where to Find Active Directory Lockout Policy
Active Directory lockout policies are controlled in the “Group Policy Management” settings. You can view and edit the policies by several methods: Server Manager, Windows Command Line / Powershell, and Windows Search.
1. View Policy Using Server Manager
Navigate to Server Manager on the Domain Controller > Tools > Group Policy Management
Under Forest > Domain > Your domain.local > Default Domain Policy > Right-Click > Edit
In the Default Domain Policy Management Editor Console click on Computer Configuration dropdown > Policies > Windows Settings > Security Settings > Account policies > Account Lockout Policy
By default, Windows does not set a threshold value.
2. View Policy Using Command Line or Powershell
Open and Elevated Windows Command Prompt or Windows Powershell and type the command:
net accounts
3. View Policy Using Windows Search
Entering “group policy” into windows search will bring up the Group Policy Management Editor Console directly.
What Do Active Directory Lockout Policy Settings Mean
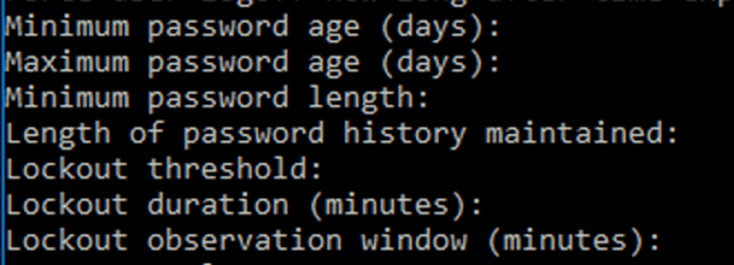
Minimum Password age: The minimum number of days a user must keep a password before they can change it.
Maximum Password age: The number of days before the user would need to change the password after the system requests to do so.
Maximum Password length: The number of characters in the password.
Length of password history maintained.
Lockout threshold: The maximum number of failed log-in attempts before an Active Directory account is locked out.
Lockout duration: The length of time that an Active Directory account will remain locked without being manually reset.
Lockout observation window: The amount of time Active Directory looks for the lockout threshold. This resets after every observation window.
How to Check if an Active Directory Account is Locked
Unlocking a user account requires action from an administrator – often becoming a time consuming and inconvenient daily task. There are multiple different reasons for Active Directory Lockouts to happen, from an individual user forgetting their password to malicious activity by a hacker. You can view current AD lockouts using Event Viewer and Powershell.
1. Viewing AD lockouts using Event Viewer
Navigate to the Domain Controller and search Event Viewer in windows search
Click on Windows Logs > Security
Click on Filter Current Log. In the Filter Current Log Window in the Event ID Section, type:
4740
You should see all the lockout events.
Click on any event to view more details such as the computer name and the username.
2. Viewing AD lockouts using PowerShell
You can use the Search-ADAccount Powershell cmdlet to find information about the locked-out accounts.
Open an elevated Windows PowerShell and type the command:
Search-ADAccount -LockedOut
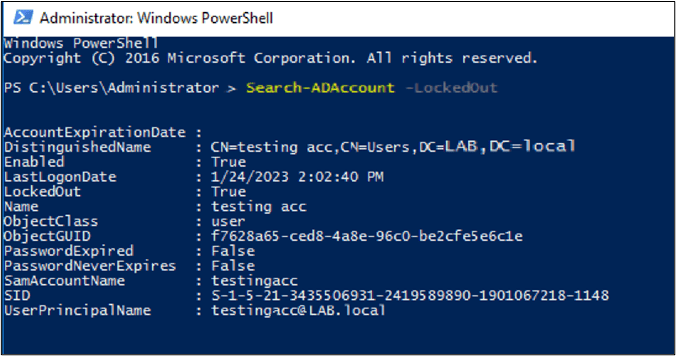
This command will retrieve all the locked-out accounts.
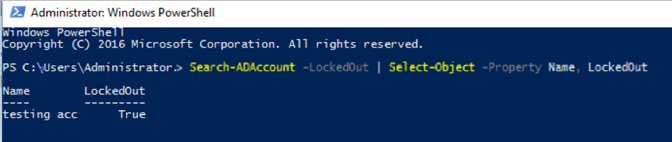
To view all locked out accounts:
Search-ADAccount -LockedOut | Select-Object -Property Name, LockedOut
How to Change the Number of Tries Before Active Directory Lockout
Windows security baselines recommend configuring a threshold of 10 failed log-in attempts. A higher threshold can prevent accidental account lockouts and reduce the demand on IT staff to manually unlock accounts. However, a lower threshold is more secure. You can change the number of attempts before a lockout using Command Line or Powershell.
Open Powershell or Command Prompt and type the following command, where n is the number of attempts:
net accounts /lockoutthreshold:n
How to Change Active Directory Account Lockout Duration
Open Powershell or Command Prompt and type the following command, where n is the number of minutes:
net accounts /lockoutduration:n
(Note: if you put 0, this will lockout the user till the administrator can manually release)

