2024 H1 Cumulative Update for Exchange Server
Microsoft announced the availability of the 2024 H1 Cumulative Update (CU) for Exchange Server 2019 (aka CU14). CU14 includes fixes for customer reported issues, a security change, and all previously released Security Updates (SUs).
Extended Protection enabled by default
As announced in August 2023, by default, starting with CU14, Setup enables the Windows Extended Protection (EP) feature on the Exchange server being installed. This will happen when running the GUI version of Setup and when running the command line version of Setup without using either the /DoNotEnableEP or /DoNotEnableEPFEEWS setup switch to opt out. Please see the EP setup documentation for more information.
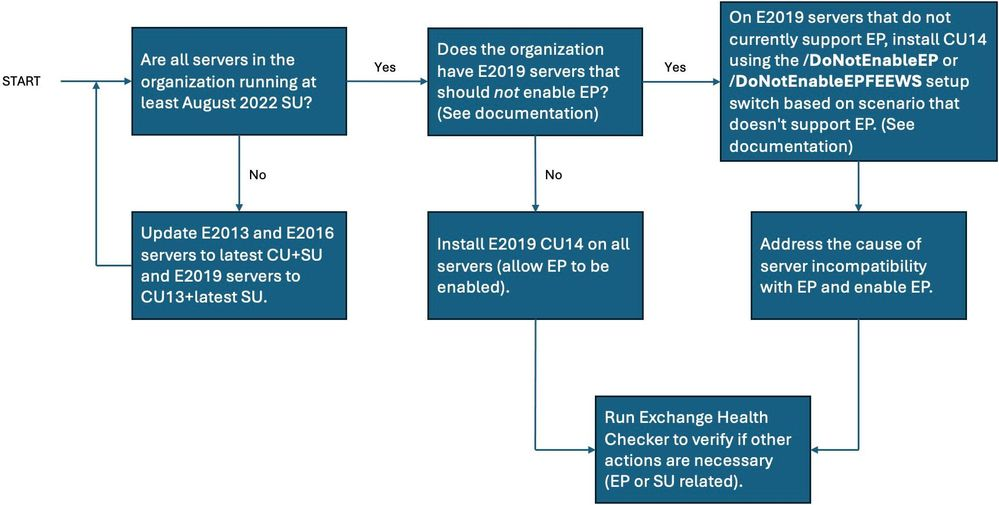
While Setup enables EP by default, it does not validate that your organization is ready for or able to use EP. To validate that your organization is ready, please review the following before running Setup:
- Exchange Server Health Checker script
- Prerequisites for enabling Extended Protection on Exchange server
If your servers are not ready for using EP (for example, they use SSL bridging or there are mismatches between client and server TLS configuration), and you do not opt out of EP enablement during Setup, it is possible that some functionality may break after installing CU14. If that happens, you must either make the configuration changes to fulfill the prerequisites for EP (recommended), or use the EP script to disable EP on this server after Setup has completed (and in the future, use the Setup switch to opt-out of EP on all servers that do not yet meet EP prerequisites).
That said, Microsoft originally released Exchange Server EP support in August 2022. If you haven’t enabled EP yet, it is time to take this step and further secure your Exchange server environment. Additional information can be found in the documentation.
To help you decide how to proceed, Microsoft has provided the following decision flow:
NET Framework 4.8.1 support on Windows Server 2022
CU14 also introduces support for .NET Framework 4.8.1, which is only for Windows Server 2022 (and it cannot be installed on older versions). The Exchange Server supportability matrix has been updated to reflect this change.
TLS 1.3 support moved to CU15
Microsoft previously announced plans to support TLS 1.3 when running on Windows Server 2022 in CU14. They are still testing and validating TLS 1.3 with Exchange Server and do not want to delay the release of CU14. Support for TLS 1.3 will be released in CU15 later this year.
CVE-2024-21410 information
To address CVE-2024-21410 (also released today) – please allow CU14 Setup to enable Extended Protection (EP) on your Exchange 2019 servers. On all other versions of Exchange that support it, enabling EP addresses this CVE. Please see Configure Windows Extended Protection in Exchange Server.
If you have servers that currently do not meet the prerequisites for EP, please see the following table:
| Scenario that does not support EP | Action to take |
| SSL Offloading for Outlook Anywhere | SSL Offloading for Outlook Anywhere must be disabled. If Extended Protection is enabled via Exchange Server CU14, the installer will take care of disabling SSL Offloading for Outlook Anywhere. |
| SSL Offloading on Load Balancer | SSL Offloading is not supported. Use SSL bridging instead with the same SSL certificate as on Exchange Server IIS front end. |
| Public folders hosted on Exchange Server 2013, 2016 CU22 (or older) or 2019 CU11 (or older) | Move all Public folders to currently supported versions, decommission Exchange Server 2013 which is out of support. Check this table for your Public Folder scenario. |
| Modern Hybrid agent is used to publish Exchange Server to the internet in hybrid scenario | Identify the Exchange Servers which are published via Modern Hybrid agent, by following the steps outlined in this section of documentation.On these servers, run Exchange Server CU14 setup in unattended mode and use the /DoNotEnableEPFEEWS switch to not enable Extended Protection on the EWS front end virtual directory. |
Please note that CVE 2024-21410 also applies to Exchange Server 2016. For Exchange 2016 servers, follow Configure Windows Extended Protection in Exchange Server if Extended Protection is not already enabled in your organization.
Release details
The KB article that describes the fixes in this release and product downloads is:
- Exchange Server 2019 Cumulative Update 14 (KB5035606), VLSC Download, Download
After installing a CU, always check for and install any available SUs. The Exchange Server Health Checker will also tell you if any additional steps are needed.
Support status
With the release of Exchange Server 2019 CU14, CU12 is no longer supported and will not receive any future SUs. Please update your servers to the latest CU to continue receiving SUs. As of this writing, the support status of different Exchange versions is as follows:
| Exchange Server | Support status | Action to take |
| Exchange 2019 CU13 or CU14 | Supported | Update to latest SU |
| Exchange 2019 CU 12 (and earlier) | Unsupported (no future SUs) | Update to latest CU and latest SU |
| Exchange 2016 CU23 | Supported | Update to latest SU |
| Exchange 2016 CU22 (and earlier) | Unsupported (no future SUs) | Update to CU23 and latest SU |
Exchange Server 2019 is now in Extended Support, and as previously announced, Microsoft plan to release one more CU for Exchange Server 2019 (2024 H2 CU, aka CU15).
Additional information
Microsoft recommends that all customers test the deployment of an update in a lab environment to determine the proper installation process for their production environment.
You can find information on preparing Active Directory here. All Exchange-made schema changes are tracked here.
For installation best practices, see Upgrade Exchange to the latest Cumulative Update. See also the Exchange Update Wizard for detailed installation steps.
If you plan to install the update in unattended mode from PowerShell or a command prompt, make sure you specify either the full path to Setup.exe, or use a “.” in front of the command when running Setup directly from the folder containing the CU. If you do not do either of these, Setup may indicate that it completed successfully when it did not. Read more here.
Customers in Exchange hybrid deployments and those using Exchange Online Archiving with an on-premises Exchange deployment are required to deploy the latest CU for product support.
For the latest information on Exchange Server announcements please see What’s New in Exchange Server and the Exchange Server Release Notes.
Reach out to Messageware to improve your Microsoft Exchange Server Security
If you are not protecting all the protocols used by your Exchange Server, you’re putting your company at a higher risk of a data breach.
Security incidents happen frequently. They cause disruption, loss of data and potentially risk the reputation of your company. However, if you implement these steps, you’re doing more than most other companies.
Have you heard about Messageware’s EPG that offers advanced Exchange Server security to protect organizations from a variety of logon and password attacks, as well as extensive real-time reporting and alerts of suspicious logon activity? Click here to learn more.
