AD account lockouts can be disruptive and frustrating for users, support staff, and administrators. However, they play a crucial role in security by preventing password guessing through repeated login attempts, such as brute force attacks. Without the protection provided by account lockouts, passwords could eventually be compromised, leading to unauthorized access.
This step-by-step guide will help administrators understand how the Windows Event Viewer serves as an essential tool for effectively diagnosing and resolving these security incidents.
Preparing for Event Log Access
Prerequisites and Access Rights
- Domain controllers contain the authentication logs that need to be examined
- Log onto the Domain Controller with an account with administrative privileges.
- Verify the system’s Date and Time settings are correct, as inaccurate timestamps can lead to confusion during log reviews.
- Verify Audit policies are enabled on the server to log authentication events. Check and configure audit policies in the Group Policy Editor under: “Computer Configuration” / “Windows Settings” / “Security Settings” / “Advanced Audit Policy Configuration”
Account Lockout Discovery
There are several ways to check for account lockouts. We’ll use these two:
- Event Viewer
- PowerShell
Method 1 – Event Viewer
Open Event Viewer:
- Click on the Start button, type “Event Viewer”, and press Enter.
- Alternatively, you can press Win + R, type eventvwr.msc, and press Enter.
Navigate to the Security Log:
- In the Event Viewer, expand “Windows Logs” in the left pane.
- Click on “Security” to open the Security log
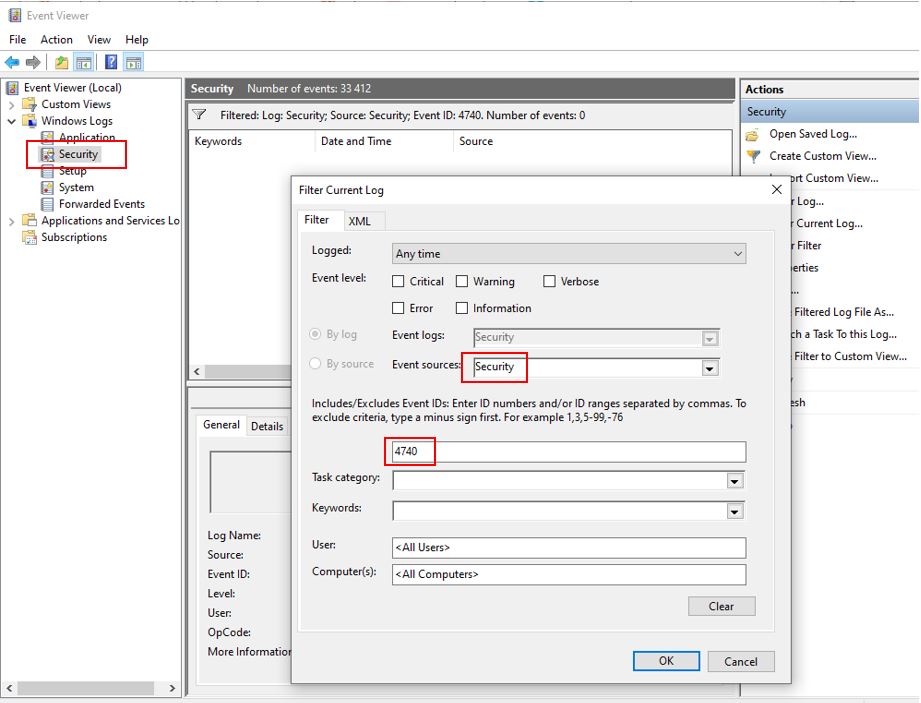
Filter for Account Lockout Events:
- Right-click on the “Security” log and select “Filter Current Log“
- In the “Filter” tab, in the “Event sources” dropdown, select “Security“.
- In the “Event IDs” field, enter the Event ID 4740 for account lockouts
- Click “OK” to apply the filter.
Review the Events:
- Browse through the filtered results to find specific account lockout incidents
- Double-click an event to see event details, such as the User Account, Time, and Caller Computer Name
- Caller Computer Name: This can often tell you where the lockout request came from, which can be helpful in identifying the source of repeated lockouts (such as a mobile device, mapped drive, service, or a specific application).
- Account Name: The locked-out user account
- Logon Type: Whether the attempted login was interactive (e.g., direct login) or network (e.g., remote server access)
- Failure Reason: Indicates why the login failed (e.g., bad password, account disabled).
Method 2 – PowerShell
Using PowerShell to Check for Account Lockouts :
- For advanced users, PowerShell can be used to query and filter event logs.
- This command retrieves entries in the Security log where the Event ID is 4740
Get-EventLog -LogName Security | Where-Object {$_.EventID -eq 4740} | Format-ListFor a more detailed look at using PowerShell to check for account lockouts see our guide to Using PowerShell to Find and Unlock Active Directory Account Lockouts.
Resolving Account Lockouts – Additional Investigation
Use the information from the event details to investigate why the lockout occurred. Common causes include user error, outdated credentials on devices, or malicious attempts.
- Event Timeframe: Focus on events from the period around the reported lockout issue.
- Filter by Username: If you suspect a specific user, filter the log by their account name.
- Additional Event IDs: Event IDs 4741 and 4771 can provide further context on failed authentication attempts and Kerberos issues.
- Audit Account Lockout Events: For better tracking, ensure account lockout events are enabled in the Domain Security Policy.
Once you’ve resolved the underlying issue, you can unlock the account either through Active Directory Users and Computers (ADUC) or via PowerShell.
Preventing Future Lockouts
1. Account Lockout Configuration
- Increase the lockout threshold to tolerate a small number of mistyped passwords.
- Set a reasonable lockout duration (e.g., 30 minutes), so accounts reset automatically.
2. Identify the Root Cause
- Check event logs on Domain Controllers to find the source of failed login attempts (device, user, service, etc.).
- Use auditing tools for advanced troubleshooting.
3. Limit Concurrent Logins and Services
- Restrict how many times a user can be logged in at once to prevent old devices from causing issues.
- Ensure all automated services, scripts, and scheduled tasks use up-to-date credentials.
4. Strong Password Policies to help keep Passwords safe
- Enforce complex passwords that are difficult to guess (length, combination of characters).
- Implement regular password changes.
- Note: strong passwords do not actually reduce Account Lockouts but they do help ensure passwords are not guessed, reducing the chance of system compromises
5. User Education
Train users on good password practices and the importance of updating credentials across all devices.
6. Install a Security Solution
Installing a security solution like Messageware EPG for Exchange Server. EPG has an intelligent independent locking mechanism that leaves your users operational while banning the actual attack sources.
Strengthen Your Server Security with Messageware
Data breaches have increased by 72%, servers are compromised in under 90 minutes. Ensure you have multiple layers of security software protecting your Windows Servers.
Messageware offers powerful security solutions, including:
Z-Day Guard for All Windows Servers: Next-gen server protection, providing detection, alerting, and response (MDR) to zero-day and server penetration cyber-attacks. Leverages embedded monitoring technology that cannot be turned off by malicious software. No need to research complicated deployments and no learning curve to install and manage.
EPG Guard for Exchange Servers: Real-time security stops AD account lockouts, eliminates brute force password attacks, provides intelligent GEO blocking, and prevents Exchange Server vulnerability probing. Enhance security through real-time collection and analysis of logon information, with advanced reporting, threat detection, and security controls.
Don’t leave your critical infrastructure vulnerable, be proactive and stay ahead of evolving threats.
